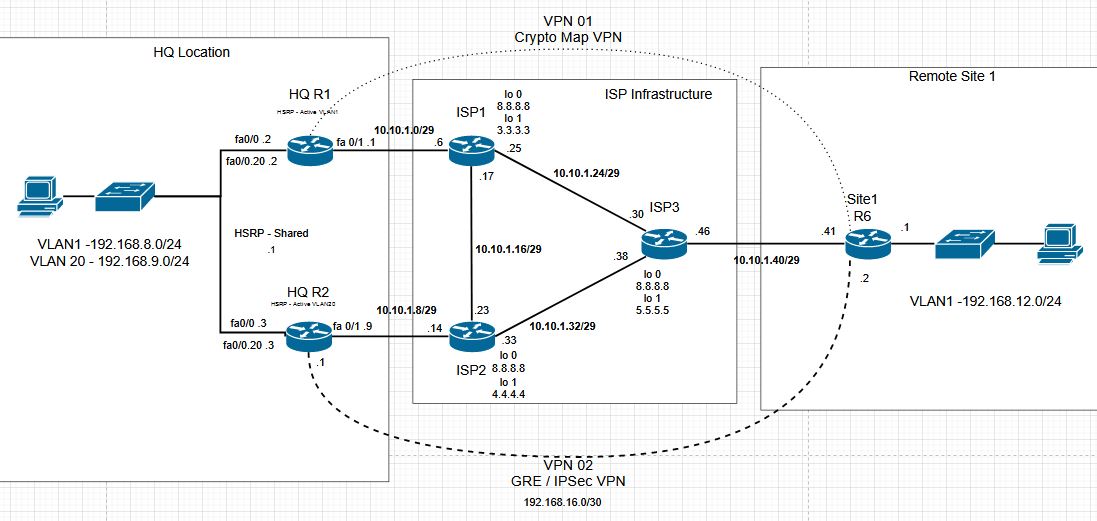
CCNP Topology Adding EIGRP
To improve the network we will add EIGRP as an IGP, and replace the static routes on the VPN 2. This will allow us to use the VPN 2 as our primary VPN, while using the crypto map VPN as our backup.

HQ R2 Configuration
To complete this set up, we will be working on R1, R2, and R6 at the remote site. Set up on R2 is shown for simplicity.
To start, a new key chain is needed for use with EIGRP authentication. Our EIGRP AS number will be 120, so we will use that number for our key.

Next, we will create a new interface on R2 and R1 (VLAN 30), and use this to peer the routers with EIGRP. The interface is shown here with authentication configured for EIGRP AS 120.
Although end user facing networks will be distributed with EIGRP, the interfaces are configured as passive. This is for security reasons, as we don’t want our routing advertisements, or authentication hashes, going to end hosts. VLAN 30 was created for peering, because we don’t have any end hosts on that network.

We have modified the old static route to an AD of 254, so it will take precedence if EIGRP is down, but is effectively removed from the routing table, if the VPN is up and EIGRP is working. Passive interfaces are also configured towards the end user VLANs, and network statements are configured to include needed interfaces.

Once the EIGRP is configured, we can add the authentication to the interface and move on to verifying it is working correctly.

Verification of EIGRP
The “show ip eigrp interfaces” verifies EIGRP is running on both tunnel 0 and the VLAN 30 sub-interface.

Next, verification of neighbors shows, that both R1 and R6 are neighbors, and our queue count is 0.

We will move to R1 to verify routes and test connectivity. R1 has a route to both the GRE tunnel network, and the remote site. The next hop for them is the R2 router Fa 0/0.30 interface. This shows that now even if HSRP is forwarding on R1, traffic needing to go to the remote site will be sent to R2, and use the VPN 02 for transit.

ICMP shows that we can reach the remote 192.168.12.0/24 network, and a trace route shows that traffic is moving through R2 to get there.


As a last note, classic EIGRP mode was used here because the lab doesn’t support EIGRP named made. I do have the ability to set up a newer lab, and will do so for some future topics.