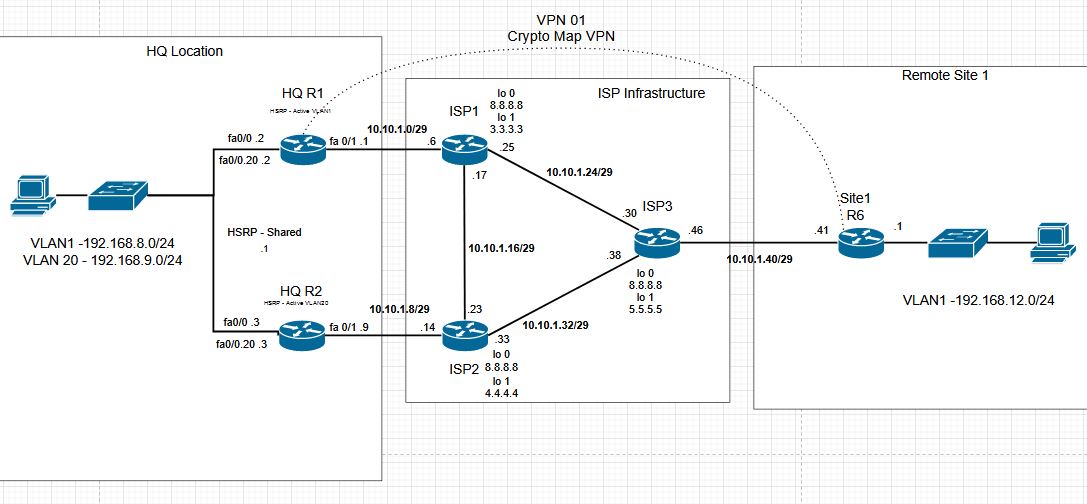
CCNP Topology VPN 1
To establish connectivity from our remote site 1 to the HQ site, we will start with a crypto map style VPN. Although there are better alternatives, this is the most popular VPN I see. Generally, if it is not required for vendor compatibility, I would go with routed VPNs. They are less prone to miss configuration, and more advanced VPNs will be formed as overlays using routed VPN technologies.

The VPN will only be from the Site 1 router to the HQ R1 router. We will show a routed option to HQ R2. The two sides of the VPN will be mirrored, so we will only show the R6 side of the VPN. Once configured, we will verify the VPN is moving traffic in both directions.
Phase 1 Policy
Phase one is going to provide an initial encrypted connection, and as a simplification can be thought of as a parent tunnel. It will be used for the VPNs control plane. In the settings we can see that we create a policy, assign an encryption, authentication method, the DH Group, and (not shown) a hash function.

Access List Changes
A crypto map style VPN uses a proxy access list to control traffic that will be encrypted. There will be two access list configurations made. One to identify traffic, and the second to make sure the traffic is excluded from NAT. Below, we see all traffic from the local network to the two networks at the HQ are allowed on the VPN, and are denied by our new NAT ACL entry.

Phase 2 Policy and Crypto Map
The phase 2 policy (transform-set) is used to specify encryption type and authentication hash used for the VPN. The ACLs and VPN configuration all get tied together in a crypto map. This identifies the peer we are connecting to, the transform-set, and the ACL being used to identify traffic.

Apply the Crypto Map and Verify
To activate the ISAKMP function, the crypto map is applied to the outbound interface.


The tunnel is initialized by sending traffic to the HQ site. Then the phase 1 and phase 2 statistics are verified to make sure the tunnel is working. The packets are sent from an inside interface, so they activate the tunnel. We can see the phase 1 SA is in QM_IDLE state, and that packets were encapsulated and decapsulated. Our first VPN is up and working.